NetBull Keylogger - User Guide
Installation
NetBull keylogger is a portable (standalone) program designed to run without being installed in the classic way (by running a setup or installer file), it runs from wherever you place it. Basically there are 2 parts to the software, "NetBull.exe" (the main program) and "module.exe" file (the actual keylogger). From the main NetBull program you have to build a "module" (see "Build Module" button) with the settings you want (email log delivery etc.) and that "module" must be run/doubleclicked on the computer you want to monitor.
So, to install the keylogger you have to doubleclick/run the "module" file (it's not enough to only build it) on the computer you want to monitor. After doubleclicking/running the "module" file, the keylogger is auto-copying in the system and runs from there in stealth mode.
NetBull keylogger can be installed on any computer running Windows 2k/XP/Vista/Windows 7/Windows 8/Windows 10/Windows 11 (32-bit and 64-bit).
Main Options

The "module" icon can be set to any of the icons included in NetBull or another icon of your choice. The icons included in NetBull are small (16x16px and 32x32px and 256 color depth), so it could be a good idea to use a bigger icon. Sometimes a big icon (more than 100kb) will be likely to lower the keylogger detection probability.
On the "Main Options" panel you are able to set the name for the "module" (the name used when the keylogger is installed in the system). The "module" is always saved as "module.exe", the chosen name will be used only when the leylogger is installed.
The easiest way to uninstall the keylogger is with a hotkey (the default is CTRL-ALT-F5). You have the option to not use any hotkey and in that case you have to manually locate and delete the keylogger file.
The "module" can be configured to be active only after the system restart or after a specified time. These "delays" can be useful under specific circumstances, by example if you want to bypass a firewall.
The "Default Settings" button will restore all the settings to NetBull default values.
↑ top of page
Logs Delivery
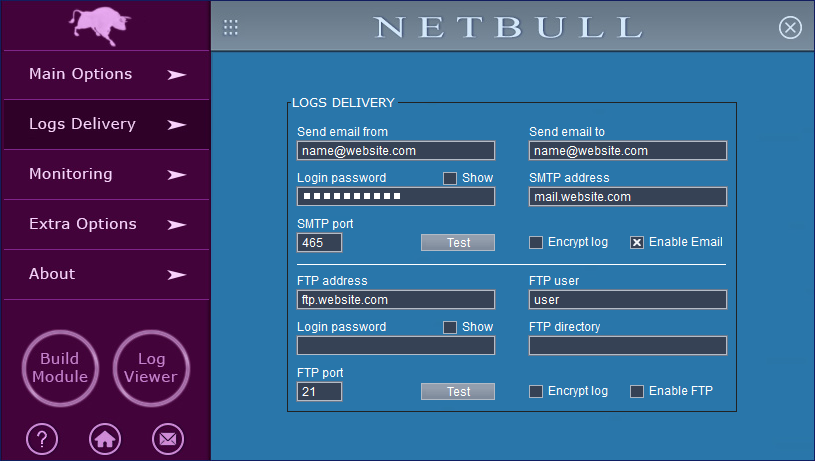
The logs/reports can be delivered by email or by FTP. The log delivery feature can work with different email/FTP providers, you don't need to purchase email/FTP accounts from us, but you should know the paid-for accounts are more reliable than the free ones.
NetBull is able to use SSL (Secure Sockets Layer - a protocol that provides secure message transmission on the Internet) for the outgoing emails. SMTP protocol typically uses port 465 for SSL connections and ports 587 and 25 for non SSL ones. The most important thing is the email address on "Send Email From" and the SMTP. If those are working fine you can receive the logs to almost any email address (Gmail, Outlook etc.). Our suggestion is not to use a free email account on "Send Email From", the logs will be lost. The best option for log delivery is to use a paid-for email account (on "Send Email From"). Of course, not all the paid accounts will work fine, it depends on the way the accounts are configured.
After configuring the email/FTP settings, do not forget to check the corresponding "enable" option.
The encryption option should be used only in the case your account can be accessed by other people and you want to protect the logs.
Also, the local logs can be retrieved from the main NetBull application and in this case you don't have to use the email or FTP options. To retrieve the local logs, just click the dotted square on the top of the NetBull interface and select "Automatically Retrieve Logs".
Finally, the logs can be viewed in the Log Viewer (see the "Log Viewer" round button), a handy option that helps you to browse through different log sections.
↑ top of page
Monitoring
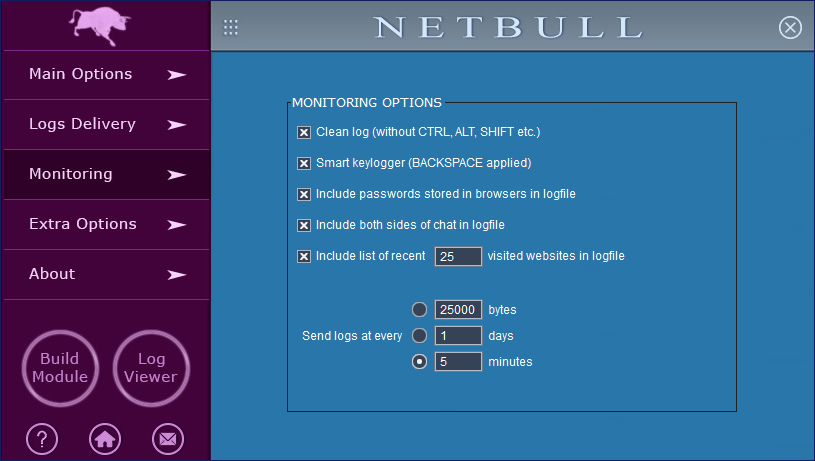
On the "Monitoring" panel you're able to adjust the keylogger monitoring and also to configure how often the logs are sent.
The "clean log" option will remove some potentially unwanted keys (CTRl, SHIFT etc.) from the log and make it more readable.
The "smart keylogger" feature applies the BACKSPACE key to the captured text and this also makes a more readable log.
NetBull is more than a simple keylogger and is able to find the usernames and passwords stored in Internet browsers (Google Chrome, Mozilla Firefox, Microsoft Edge, Opera, Vivaldi).
If the option to "include passwords stored in browsers" is checked, the keylogger will include the found usernames/passwords at the start of the log (in the 1st log in a boot session). NetBull can also include in the logs the visited websites history (for Internet Explorer and Edge) and the messenger conversations.
↑ top of page
Extra Options

On the "Extra Options" panel you can adjust the keylogger behavior.
The first extra option is to configure the "module" to delete itself after the installation.
The "module" overwriting option allows a 2nd "module" to install over the existing running "module".
A fully configurable warning window can be displayed at the keylogger run (in this way the user being aware that its activity will be monitored).
The keylogger "module" can be configured to uninstall itself after sending a number of logs. Another possibility for uninstallation is to configure the "module" to check a URL address (if the file from that URL exists the "module" is uninstalling).
NetBull keylogger can be configured to restrict the monitored user access to websites and programs. By clicking the corresponding "Configure" button you'll have the option to set the filters you want.
The "Keylogger filter" option could be handy but needs to be used carefully. If the filters are set, the keylogger will monitor only the windows (websites, programs) that have a keyword in the caption.
↑ top of page
Security
NetBull keylogger is working fine with the most up-to-date security implemented in Windows. While running the keylogger, there's no prompt from UAC (User Account Control), DEP (Data Execution Prevention), built-in Windows firewall and Windows Defender.
More than that, we guarantee the full version of the keylogger is undetectable when scanned with Norton AV, Malwarebytes, Avira, McAfee, Avast and AVG.
↑ top of page